The CIA Triad
So far, we discussed what assets we shall secure, what threats we shall secure those from, and what kinds of perpetrators impose such threats. However, we haven't talked about how to secure the assets (that is, what action we are supposed to take to keep them secure.)
To address this question, we introduce an information security model called CIA, whose principles will direct us on how to secure information-related assets we care about.
The name "CIA" is an acronym, not for the Central Intelligence Agency, but for the three pillars of this model: Confidentiality, Integrity, and Availability. It is, therefore, often referred to as the CIA Triad. We'll explore it next.

CIA logo (from the book). "Figure 3-7: CIA Triad" (page 51), Nayak, U., & Rao, U. H. (2014). The InfoSec handbook: An introduction to information security (1st ed.). APRESS.
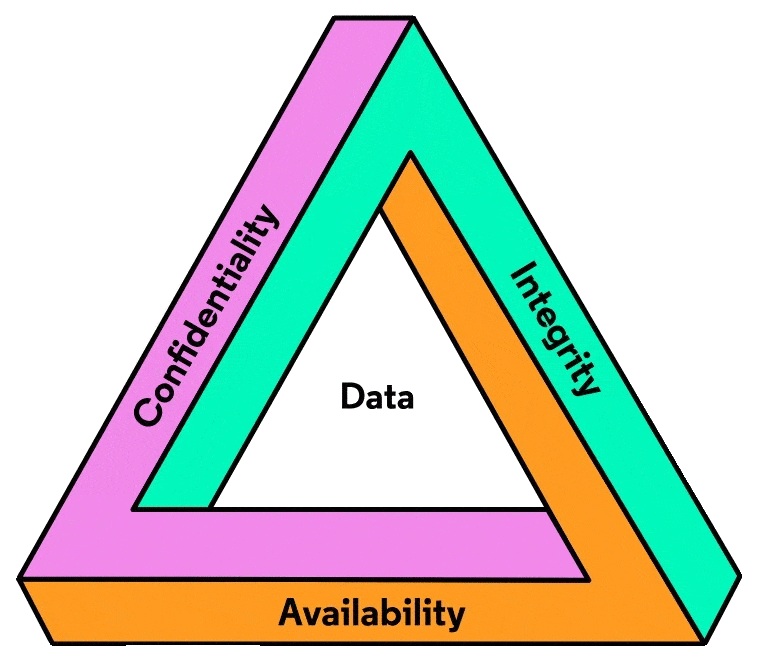
CIA logo (triangle). Taken from Codeacademy's "What is Cybersecurity?" worksheet here.
