Firewalls: Motivation
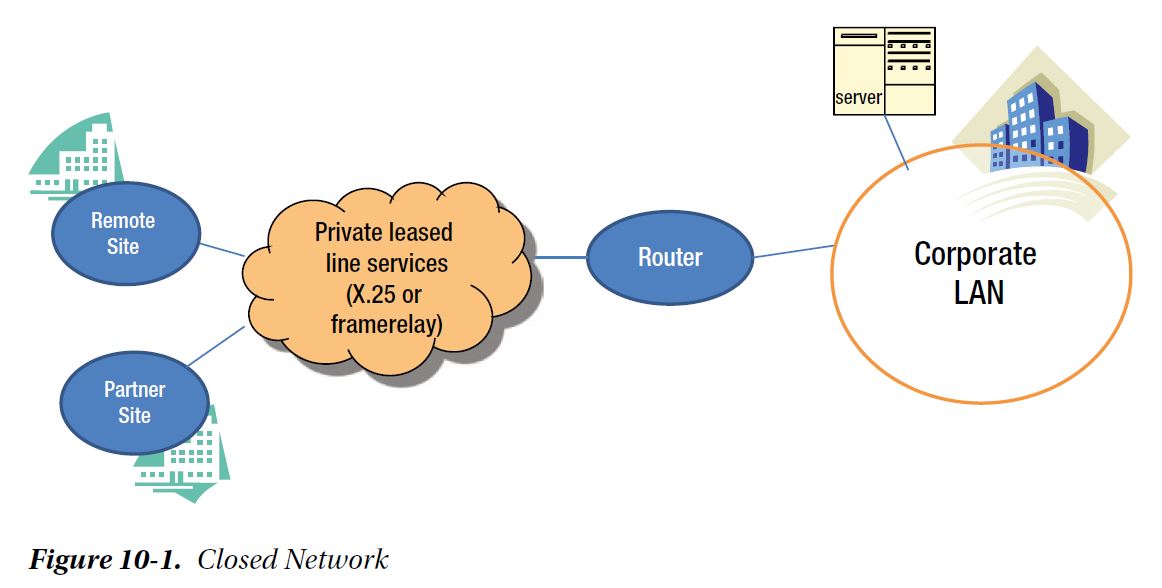
In the early days of computing, there was no outside connectivity and no World Wide Web. Networks belonging to businesses would usually implemented a closed network, which typically allowed secure access only to known parties and employees. Since no 'outsider' device was connected to such a network, there was no danger of hacking this network remotely.